Juniper SSL-VPN & Blue Coat’s ProxyClient
I posted this (via some contacts at Blue Coat) in it’s original form to the Blue Knights wiki. I thought the general population of Blue Coat users would find it useful too.
Requirement
The requirement was to provide automatically directed explicit internet access with no local break-out for Juniper SA clients. When users were disconnected from the corporate network, the requirement was to have BCWF categories blocked by default thus maintaining protection and control of access even when away from the network.
The most useful of those categories when users aren’t connected to the network are the Web Pulse categories – Spyware/Malware, Spyware/Malware Sources, Phishing and Suspicious. These categories and the Web Pulse dynamic ratings service are worth their salt and a good reason to install the client on corporate mobile devices.
In order to provide directed ‘explicit’ proxy access to the customers network when Juniper SA clients dial in, a PAC file can be distributed from the SA with the following type of configuration.
The customers environment already had two ProxySG’s, these were explicit proxies for the internal network. We added the ADN Client Concentrator functionality.
An SA2500 acted as the ‘dial in’ service for clients. A VIP (Virtual IP Address) was assigned to the ADN/Client Manager. The VIP is required because as we discovered, using the appliance’s normal explicit IP traffic wasn’t accelerated. The reason for this is that the ADN traffic needs to traverse the ADN tunnel and arrive at a device on the other side in order for the ProxySG/Client to accelerate. The VIP provides that function without the customer having to purchase a separate unit for Client Concentrator and Explicit proxy purposes.
With this information, we configure the PAC file on a host behind the SA2500. In it, we define that 127.0.0.0/8 should not be redirected, but all other traffic IS directed to ‘PROXY <proxy>:8080’.
function FindProxyForURL(url, host)
{
if(isInNet(host, "127.0.0.0", "255.0.0.0"))
{
return "DIRECT";
} else {
return "PROXY <proxy>:8080; DIRECT";
}
}
We bypass 127.0.0.0/8 because this would otherwise block the ProxyClient from functioning. Further tightening up could occur to avoid ‘Proxy Avoidance’ software from bypassing filtering.
Once this is done, we can configure our Network Connect connection profile.
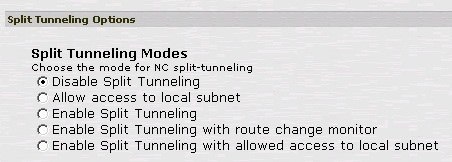
First with no split-tunneling.
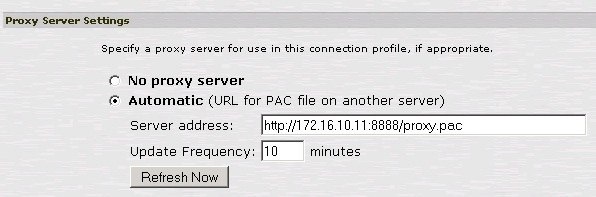
Then with the PAC file location.
For the test, I setup a new role mapping so that my proxy settings matched the PAC requirements.
With this done, we can open up the Network Connect client and connect to the network.
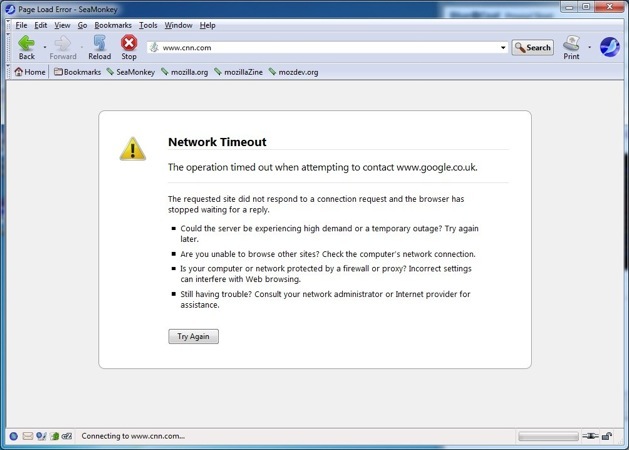
Third-party applications are blocked because no automated internet settings were provided.
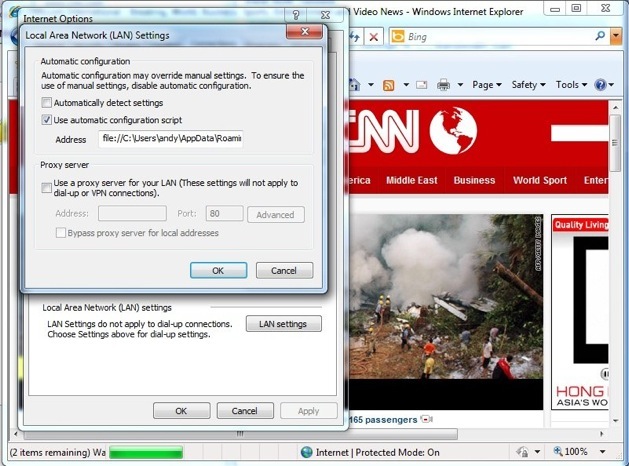
Whereas IE is able to browse because it’s been configured to use the PAC file.
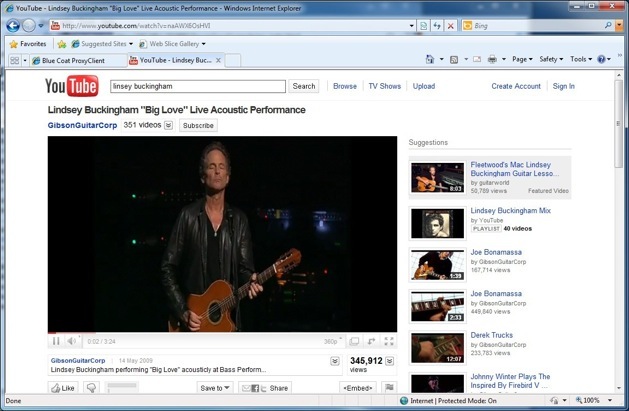
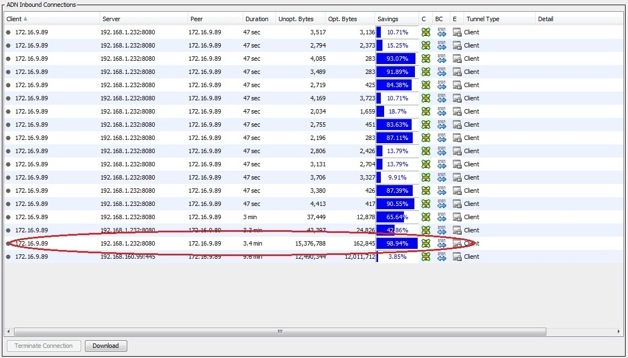
Using the VIP as our explicit proxy allows the Proxy Client to intercept and accelerate content which ordinarily can’t be cached. For example, if you were to watch your favourite You Tube video, clear the cache and reboot then connect to the SA again to watch the same video, the video should be byte-cached as in the example below.
Client side
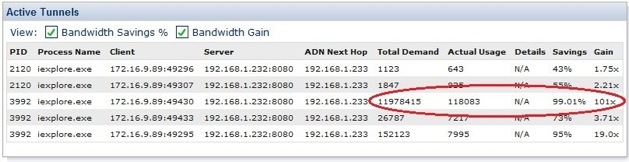
ProxySG ADN Concentrator side
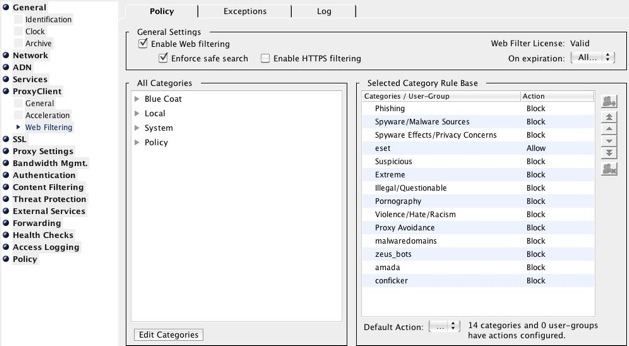
So, with the capabilities of the ProxyClient from an acceleration perspective proven, how about that requirement for control of users internet access based on categories, even when they aren’t connected to the network? Well, this is handled from the CM (Client Manager) console. Here you can define the BCWF categories (along with Local Database one’s if you use a Local DB or even other 3rd-party databases like the Internet Watch Foundation) so that they are allowed or blocked. Safe-Search can be enforced here also, along with filtering of HTTPS connections.
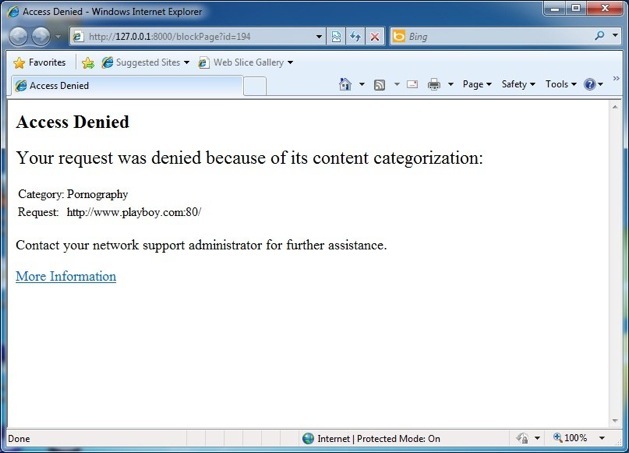
The effect is, when a user isn’t connected to your corporate network, and they attempt to view a site falling within a blocked category they’re denied access.
The Block Page can be customised to make the URL more in-tune with your corporate identity.
The ProxyClient uses the same Web Pulse cloud service as Blue Coat’s K9 Web Protection client. URL requests are submitted to Web Pulse to validate the category. Unclassified URL’s are scanned and rated on-the-fly, returning a categorisation to the client in order to make a filtering decision.
This method for corporate access provides the following benefits.
- Centralised policy control
- Reporting per-user if you have Blue Coat Reporter in use.
- Protection from malicious content via centrally published and controlled BCWF categories such as Phishing, Suspicious, Spyware\Malware Sources, and Spyware Effects when both inside AND outside the corporate extranet.
- Caching of non-cacheable content in Byte-Cache for remote workers. This includes YouTube (as above) and other streaming service such as BBC iPlayer. Under normal circumstances, this traffic cannot be cached (Pragma: no-cache is returned) or can only be cached for a short period. Using the ProxySG’s Byte-Cache we can store this content.
The same deployment type could be used when installing appliances. If the customer requires a centrally managed explicit proxy but wants ADN acceleration also (on the same box) for remote users we can use the ProxySG Manager/Concentrator with a VIP configured so traffic can ‘exit’ the tunnel at the core and be accelerated. Non-cacheable content would be stored in byte-cache.
The ProxyClient provides some great functionality in the form of WAN Optimisation but when it’s coupled with the Web Pulse cloud service for dynamic rating of URL’s it adds amazing protection to a roaming corporate device that no other WAN Optimisation vendors client can. And best of all, it’s free! The only requirement being that you have a Blue Coat appliance and a Web filter license option.