Don’t open THAT attachment!!
I run a mail service for a number of friends, mainly personal, but some business. Part of the service configuration blocks attachments which are sent where the file is a specific extension (for example exe, com, bat, scr, vbs, etc). Over the last few years, it’s done a great job in filtering out malicious stuff, but of late, I’ve started pushing the files into an Open Source sandbox called Cuckoo, for extra protection, but also the nerd factor as this sort of thing interests me, Sandboxes are great, as they allow you to execute an unknown file in a restricted environment, then view the results without it ever affecting your actual computer. Once you have the results, you can decide whether it’s safe or not. So what follows should be considered a warning – ‘Don’t open THAT attachment!’.
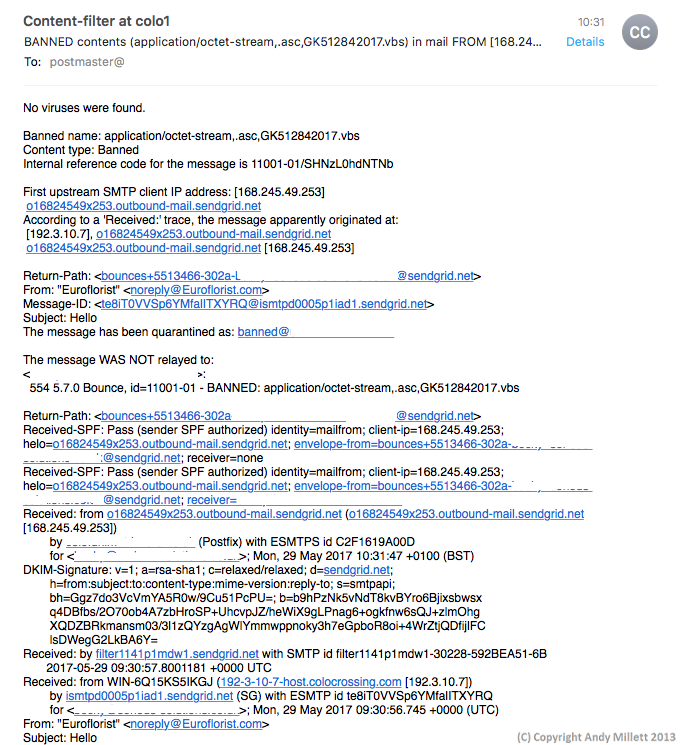
First off, here’s the mail alert –
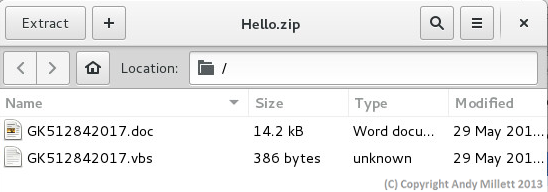
It actually looks like it’s come from a valid source, but if you look closer, you’ll see then the actual sender is IP 192.3.10.7 (owned by Colo-Crossing). Hmmmm….never-mind, we’ll push forward and take a peak at the file anyway. The actual file attachment in the mail is called ‘Hello.zip’, inside it are two files; a Word file, and a VBS script.
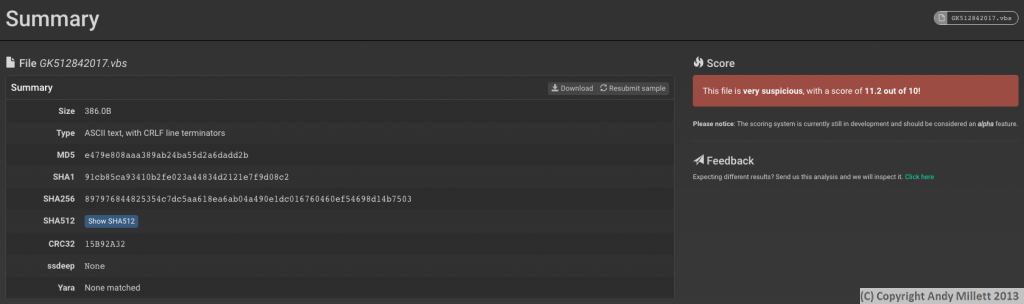
Files which are blocked are stored in a special mailbox for me to review. These files are uploaded to the Cuckoo Sandbox using a browser (no, I don’t use Windows to do this!) which is protected from running unknown scripts. Once the file is loaded, the sandbox executes it. I’ve ignored the Word file in the attachment, and instead gone straight to the VBS script. After a few minutes, the results are in –
Uh oh, a score of 11.2 out of 10 (I guess it does say the score feature is in Alpha on Cuckoo :P), I’m already suspicious. Lets see what this VBS script does.
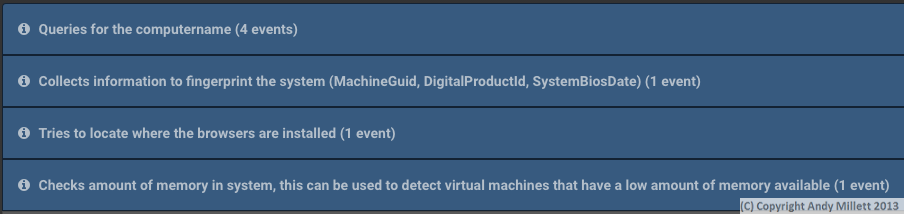
First off, it’s queried the computer name, asked about system information, queried which browsers are installed, and checked how much memory is available.
Thats suspicious, but not actually ‘doing’ anything to the system.
Next, we see the script starting to do something.
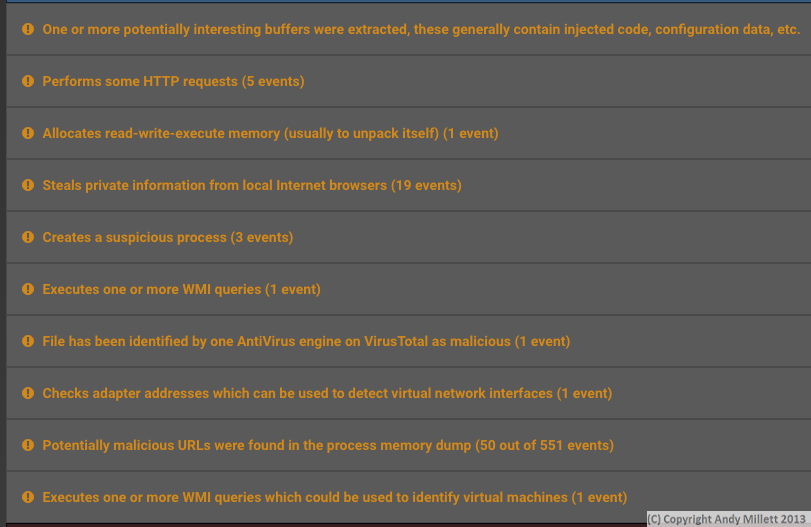
Whoa!! Now we’re getting somewhere. There’s quite a lot of things happening here, but the one which springs out to me more than any other is ‘File has been identified by one AntiVirus engine on VirusTotal’. VirusTotal, can check up to 56 AntiVirus engines, so being detected by only ONE is a serious issue. Think your local AV is going to protect you? Think again. Local AV is the last, and often worst line of defence. The script also initiates a number of outbound HTTP requests, and steals a lot of information from local browsers, as well as creating additional processes. Very scary!.
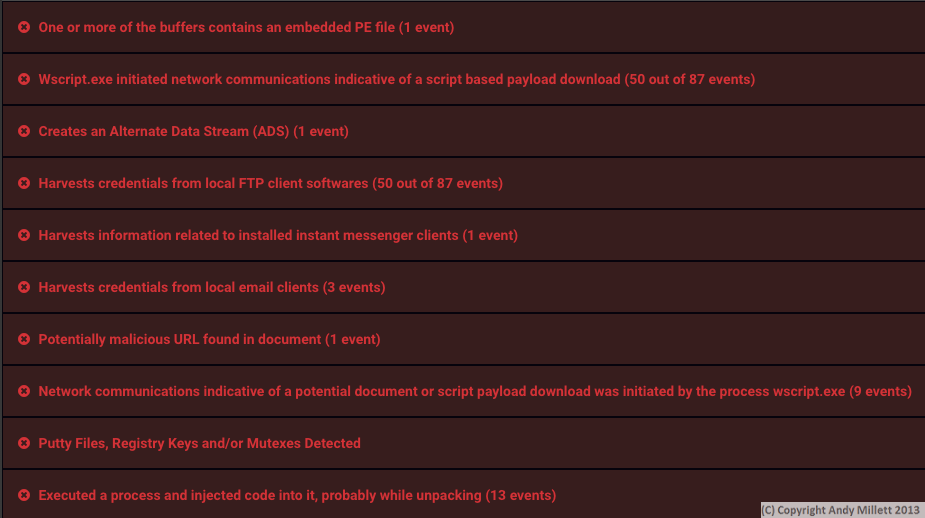
Finally, we see the real damage of the VBS script.
The VBS script now starts to do some credential stealing. Email, FTP, IM Client credentials amongst other nefarious actions, are raked from the machine. Add these to the fact it’s created a new process which is running on the computer (and will run at system startup), the computer is now something to run away from. All from opening an attachment from an unknown source.